The Extrahop Visibility Platform
Your Network Knows the Cybertruth
Are you listening?
Reveal the Unknown, Unmask the Attack.
The network is the most powerful source of truth and transparency across all assets in your enterprise—from cloud, to on-premises, to endpoints.
It sees everything, shows everything, and leaves attackers with nowhere to hide. ExtraHop gives you the full-scale network visibility you need to bring the cybertruth to light.
Reveal Everything. Miss Nothing.
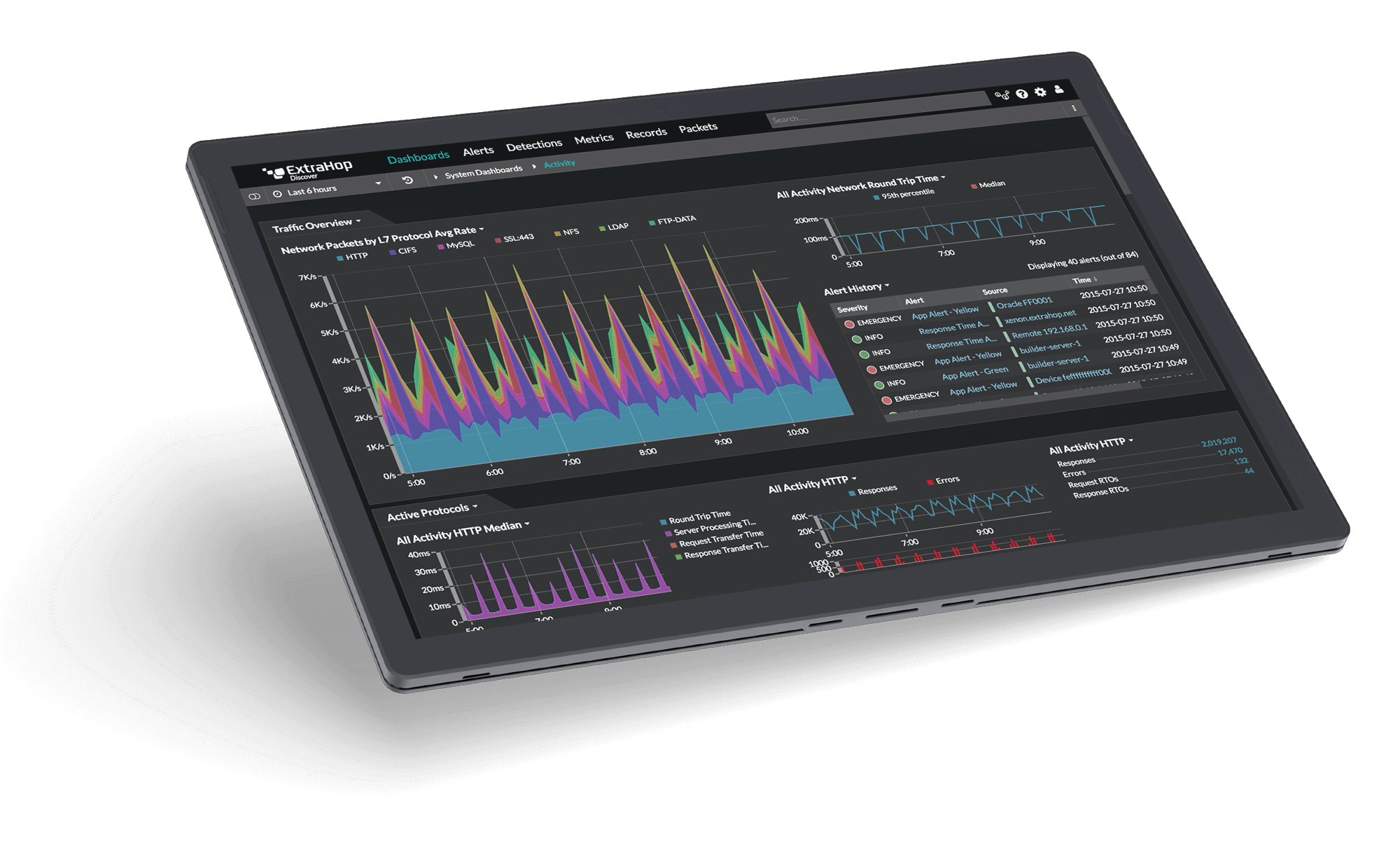
Gain Full Network Visibility
The Reveal(x) 360 platform is the only network detection and response solution that delivers the 360-degree visibility needed to see everything on your network. When organizations have full network transparency with ExtraHop, they can see more, know more, and stop more cyberattacks.
Achieve complete situational awareness and 360-degree cyberthreat visibility across the entire hybrid attack surface, from on-premises to multi-cloud to distributed workforces and operations.
Gain deep insights into threats past, present, and future through cloud-scale machine learning, robust retrospective forensics, and unparalleled decryption capabilities that uncover the cybertruth through every network twist and turn.
Detect, prioritize, and stop more malicious post-compromise activity through smarter tools that remove layers of complexity, decrease total threat response time, and save hours on each threat detection and resolution process.
THREAT
DETECTION
THREAT
Resolution
Trouble-
Shooting
SECURITY
Network Detection and Response
Use the power of network visibility and AI for real-time detection, rapid investigation, and intelligent response for any threat.
PERFORMANCE
Network Performance Monitoring
Use network data and machine learning to identify network and application performance issues and expedite time to response.
Try ExtraHop Reveal(x) 360
See more, know more, and stop more cyberattacks in real time with Reveal(x) 360 self-guided attack simulations.
Network Traffic Analysis
Network Detection and Response
Digital Forensics
Intrusion Prevention and Detection
Network Detection and Response
Intrusion Prevention and Detection
Cloud Security