NEOX Networks Solutions

Test & Measurement
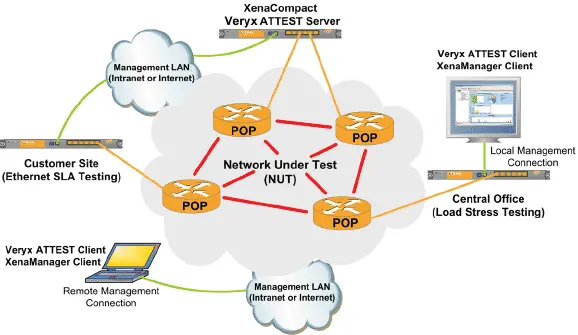
Network Conformity Testing
Xena Networks’ testing platforms have been built to test network components in laboratories and development environments. The world’s leading network equipment manufacturers use Xena’s testers.
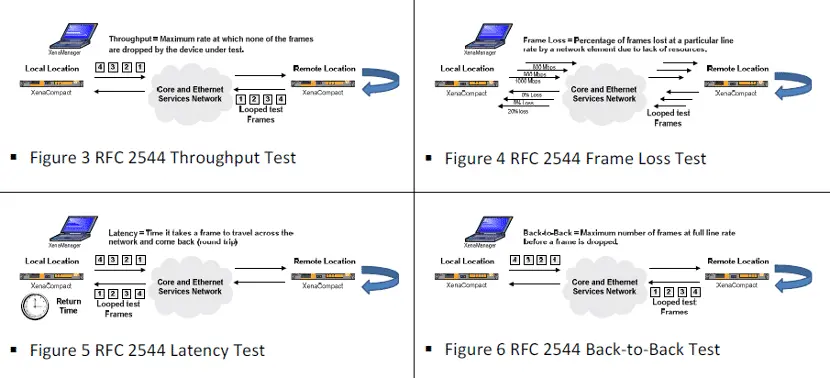
Network Load and Performance Test
Xena Networks provides a new class of professional Gigabit Ethernet testers which set new standards when it comes to price vs. performance including load and functional tests on Ethernet devices and networks.
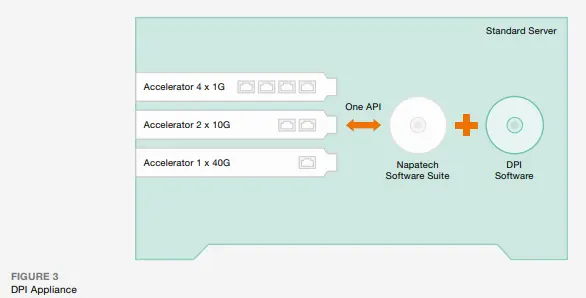
Real-Time Big Data Analytics
Real-Time Big Data Analytics (RTBDA) has emerged as a new topic in big data discussions. The concepts underpinning RTBDA can be applied in a telecom context, but it does require a rethink on what is “real time” and what sources of information can support a RTBDA strategy…

VoIP Monitoring and Analysis
Voice and video over IP present major challenges for traditional data networks. The size of VoIP and video network packets is markedly different from those of standard network applications

SD-WAN Testing
Software-Defined Wide Area Networking (SD-WAN) has become a viable and cost-effective solution for enterprises needing to connect multiple sites whilst maintaining control & transparency over the quality of the WAN circuit, in order to optimise application performance and end-user experience.
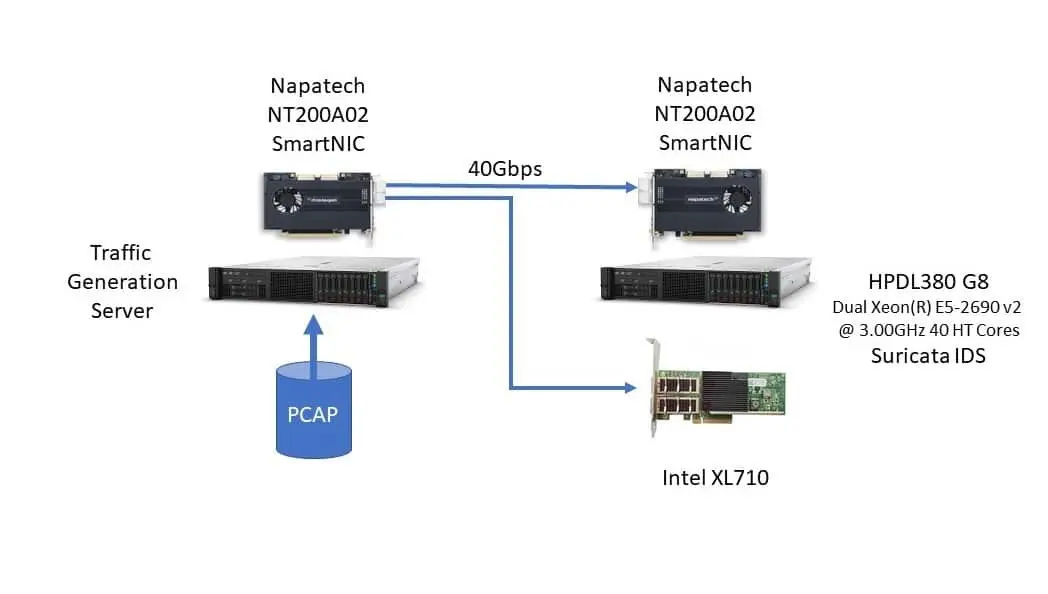
Scaling Suricata Performance to 100 Gbps
Suricata is a free open source, mature, fast and robust network threat detection engine. The Suricata engine is capable of real time intrusion detection (IDS), inline intrusion prevention (IPS), network security monitoring (NSM) and offline PCAP processing…
Network Visibility
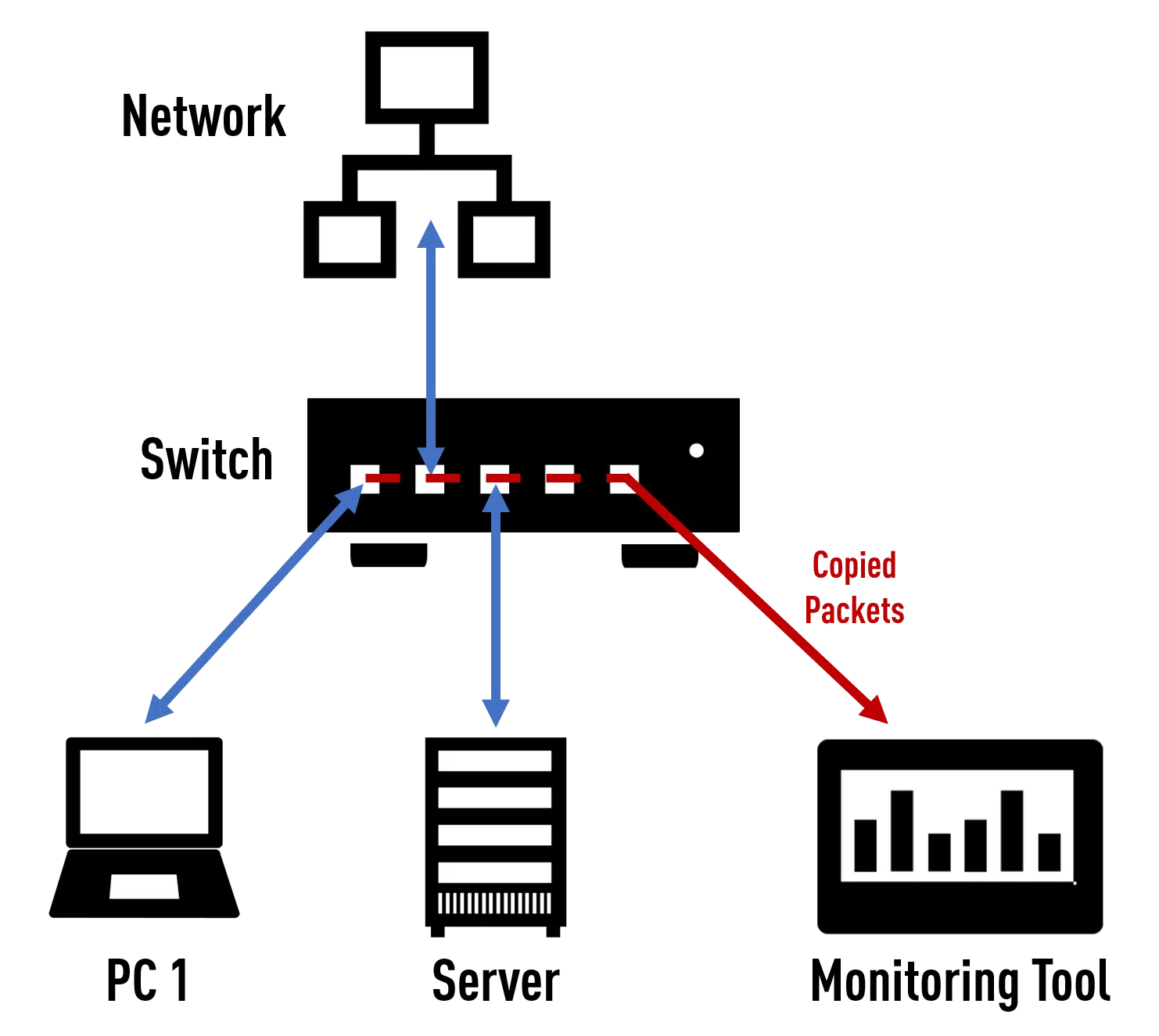
Network TAP vs
SPAN/Mirror Port
Monitoring, analysis and out-of-band security tools all have one thing in common: they need a reliable data source. But what is the best way to feed network data to these tools?
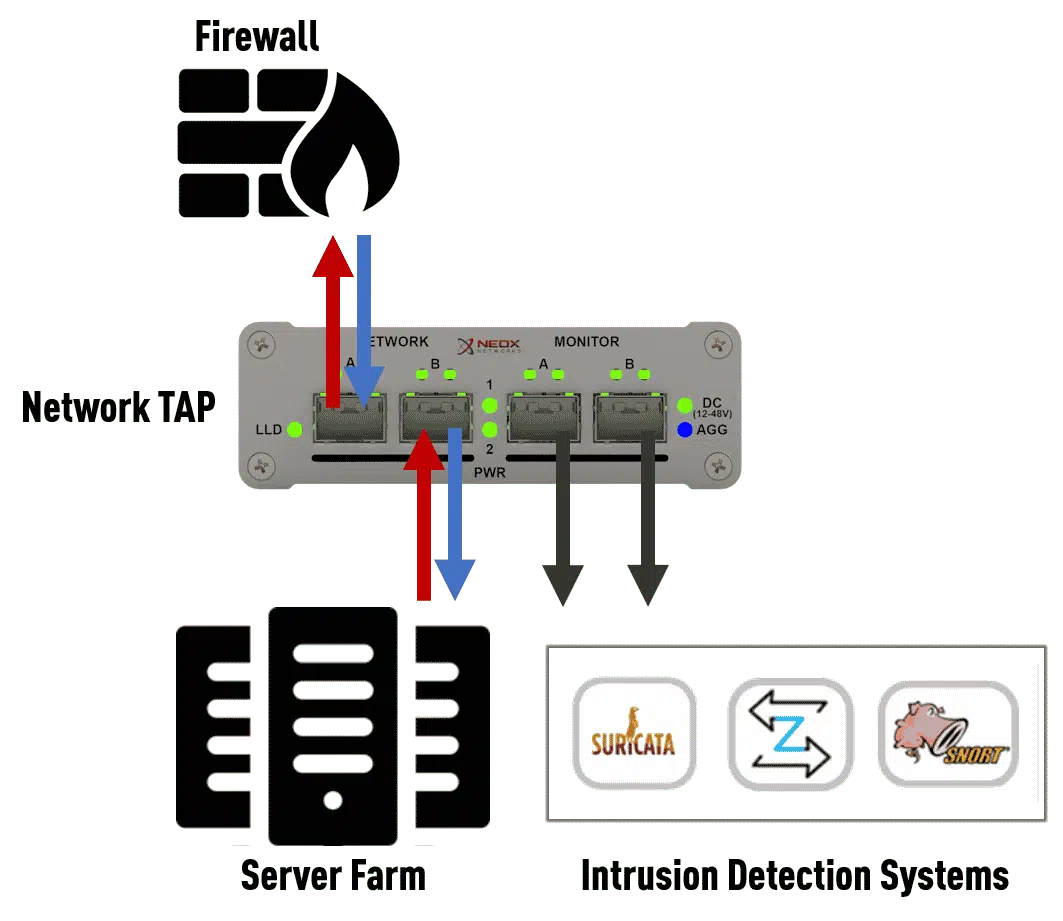
Application Examples
for Network TAPs
The classic SPAN port is definitely not a reliable data source for forensic records, because for the data to be usable in court, the integrity of the data must be ensured and data loss must be excluded…

Netflow Support
Gain insight of your network with IPFIX’s high granularity and expand your monitoring.
Supported by our PacketTiger (NG NPB) product family.

Packet Capturing
Capture a PCAP directly on the PacketTiger.
Supported by our PacketTiger (NG NPB) product family.

Packet Replay
Replay any PCAP and verify your setup instantly.
Supported by our PacketTiger (NG NPB) product family.
Why Y-cables are important for Fiber TAPs
Your Fiber TAP does not seem to work?
It is almost always due to incorrect cabling. Here you can find out what you need to consider…
Network Monitoring

Network Analysis and Monitoring
A goal of a computer is to transmit data and information of any kind between the terminals in a reliable manner. To this end, it must be ensured that the transmission of this information works smoothly even when using different protocols and operating systems…
Learn More ...
Network Security and Forensics
Corporate networks are changing. They’re becoming faster than ever and are central to every business. However, they’re also more vulnerable to attacks.

Network Forensics and Visibility Solution
Network forensics enable organizations to realize the full benefits of 10G and 40G networks: high performance with the control and security IT organizations take for granted on 1G networks. By investing in network forensics solutions, IT organizations can ensure that speed does not compromise the ability……
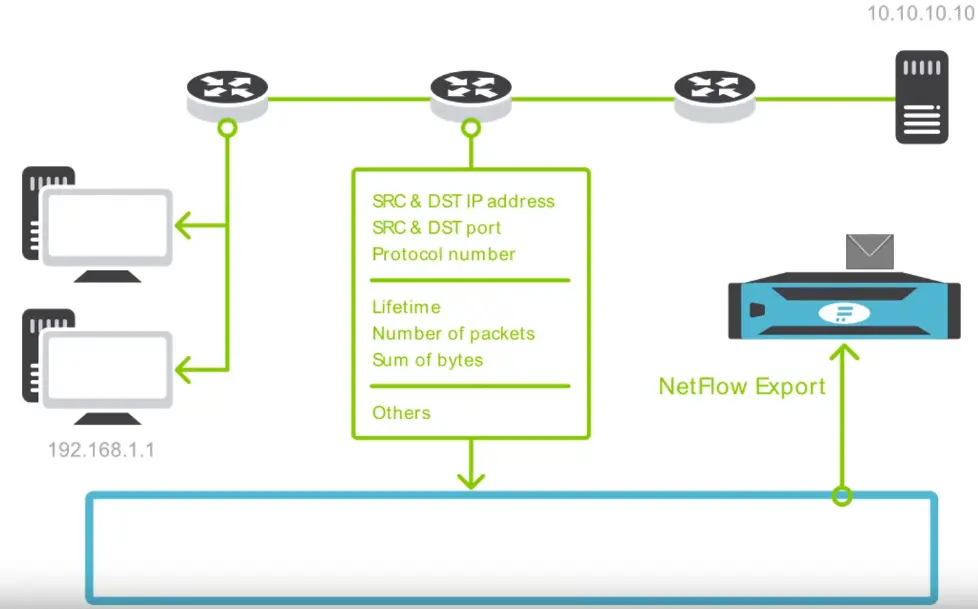
NetFlow / IPFIX Monitoring
NetFlow is an enabler of modern network management and security. It is the most widely used standard for network traffic monitoring providing network administrators, security engineers and operations managers with a deep knowledge about their IT environment.

Network monitoring
by means of Flow data
The digital transformation of corporations worldwide has led to all-pervading connectivity and high-speed data Exchange with massive productivity growths. Network infrastructure plays such a fundamental role that ensuring its reliability and security is absolutely vital for every organisation today.
Cisco Network Performance Monitoring and Optimization
LiveAction’s LiveNX provides a single network performance platform to monitor, manage, and optimize Cisco network performance by working seamlessly with Cisco SD-WAN (Viptela), Cisco SD-Access, Cisco DNA Center, Catalyst series switches, Cisco unified communications, and Cisco Meraki….

Encrypted Traffic Analysis
99% of IT professionals see encrypted traffic as a possible source of security threats. Don’t let the encrypted traffic turn into security risk. Gain a scalable visibility of threats in encrypted traffic when preserving privacy and with no impediment to latency…
Traffic Optimization

Aggregation
In this mode, the data streams are bundled and output aggregated on both of the monitoring ports.
This operating mode is supported by our PacketLion (NPB) , PacketTiger (NG NPB) and PacketRaven (TAPs) product families.

Data Masking
Hide or black out sensitive data by overwriting certain areas of a packet, no matter where that area is.
Supported by our PacketTiger (NG NPB) product family.

Deduplication
Identify and discard duplicate packets, reducing the load on your analysis system.
Supported by our PacketTiger (NG NPB) product family.

Deep Packet Inspection (DPI)
Look beyond your network directly into your applications.
Supported by our PacketTiger (NG NPB) product family.

Dynamic Load Balancing
Apart from the regular filtering options of a Network Packet Broker, they also offer an automated, load-based distribution of data, the so-called “load balancing”.
Supported by our PacketLion (NPB), and PacketTiger (NG NPB) product families.

Filtering
The Packet Broker filters control the traffic flow and can: Deny traffic, forward traffic, hand over traffic according to certain criteria and mark packets.
Supported by our PacketLion (NPB), and PacketTiger (NG NPB) product families.

GTP-Tunnel
Correlate GTP traffic with IMSI filtering and benefit from dynamic load balancing within a GTP tunnel based on the internal IP.
Supported by our PacketTiger (NG NPB) product family.

IMSI-Filter
Correlate GTP traffic with IMSI filtering and benefit from dynamic load balancing within a GTP tunnel based on the internal IP.
Supported by our PacketTiger (NG NPB) product family.

Packet Slicing
With this method it is possible to reduce the incoming data load on your analysis system by up to 87%.
Supported by our PacketLion (NPB), and PacketTiger (NG NPB) product families.

Regeneration
With this method, data packets are duplicated on x ports, so that the data of a measuring point can be made available to several analysers.
This operating mode is supported by our PacketLion (NPB) , PacketTiger (NG NPB) and PacketRaven (TAPs) product families.

Tunnel Support
PacketTiger allows the removal, termination and filtering of all common tunnel protocols.
Supported by our PacketTiger (NG NPB) product family.




