Application Examples for Network TAPs
Network forensics and data recording
Network forensics is a branch of forensic science that ensures legal evidence is preserved within computer networks. This area of forensic science uses a variety of applications, such as:
- Analysing all the network traffic of the accused person in legal proceedings
- Tracing and securing evidence found on the network
- Analysing a system after a hack or cyber attack
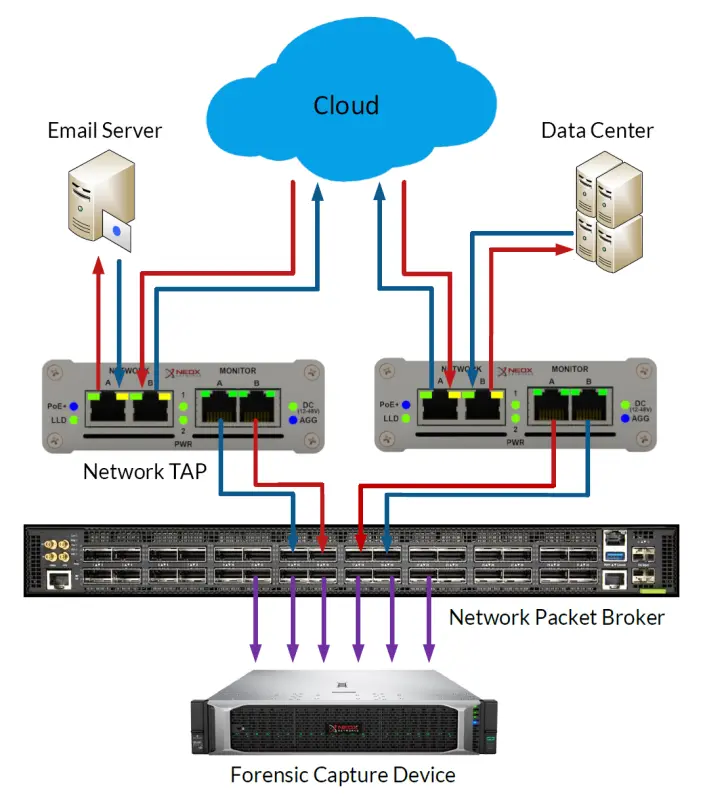
A data logger captures traffic across the whole network and can be used in court, making it something you should consider for any kind of data attack.
For forensic analysis to be 100% successful, it’s essential to have access to your network traffic. The classic SPAN port is definitely not a reliable source for forensic records because data records used in court must be integral and contiguous with no data loss for continuous analysis and evaluation by the forensic process.
For the above reasons as well as others, SPAN ports for network forensics aren’t a suitable method so experts rely on passive Network TAPs to gather their data.
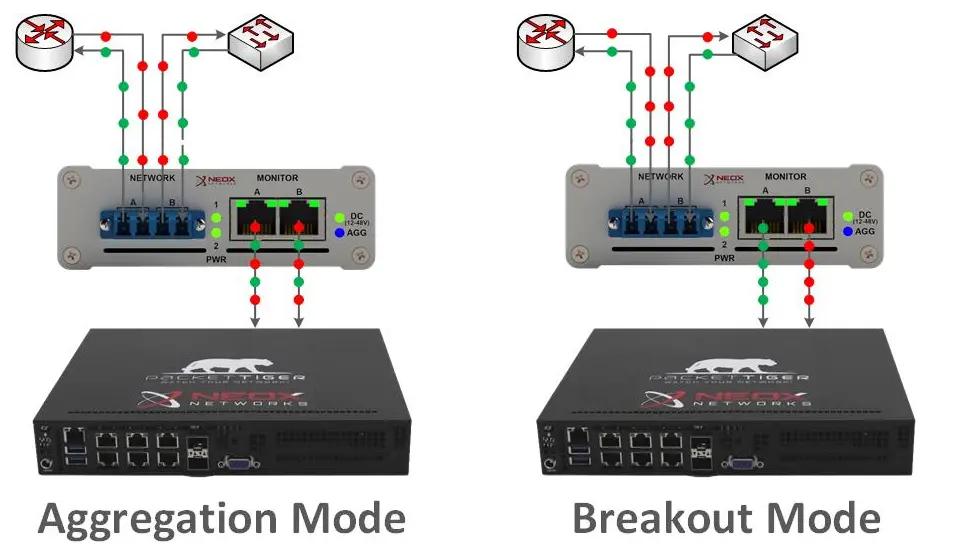
It may also be necessary to monitor multiple network segments simultaneously and to aggregate the data in the direction of your monitoring tools, or to replicate them simultaneously to more than one forensics tool. Permanent solutions can be best implemented with our Modular TAPs.
Our modular TAPs provide the definitive solution and we’re more than happy to help you to choose the right one.
Network Analysers
Having access to your network connection is essential for 100% reliable network analysis, which is something SPAN ports can’t guarantee for various reasons! When routers and switches are used, SPAN ports are adversely affected and, for performance reasons, they’re prevented from analysing critical network data. The router or switch prevents the SPAN service from doing its primary task of relaying live network traffic.
Furthermore, routers and switches don’t forward packet errors in the physical layer. Faulty packets are dropped and this changes the order in which data is sent causing network troubleshooting to be more difficult.
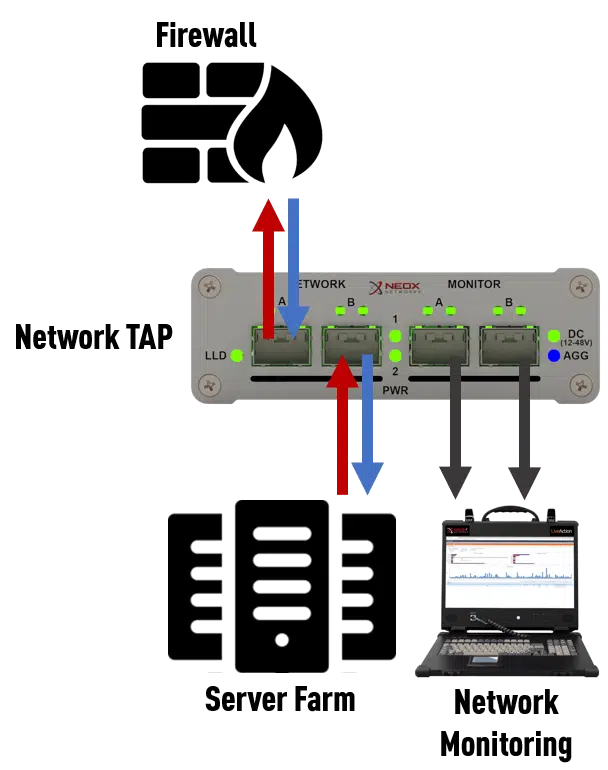
Network analysers have hardware or software applications that interpret network traffic, checking and recording it for further analysis. They’re mainly used for debugging, allowing you to analyse network problems, monitor network usage, collect network statistics for reports, and a variety of other tasks such as security monitoring.
Mobile Network TAPs are the perfect solution and meet all the requirements for network analysis Learn more about Network TAPs.
Lawful interception
“Lawful Interception” (LI) refers to legally compliant monitoring of telecommunications traffic such as voice, text, images, emails, SMS, faxes and radio cells. The evidence can be used in prosecution cases and enforced by authorised authorities. It’s also regulated by law (in Germany this is The Code of Criminal Procedure § 100a. Other countries have their own laws too).
You can install a passive access tool onto your network to resolve problems with legitimate monitoring. Using appropriate Network TAPs, data can be collected and reproduced, allowing different network segments to be monitored and sensitive data recorded using the right tools in the right areas.
NEOX NETWORKS provides network access devices that can collect network data for legal reasons. Our products help you achieve this by monitoring one or more network connections in compliance with statutory guidelines.
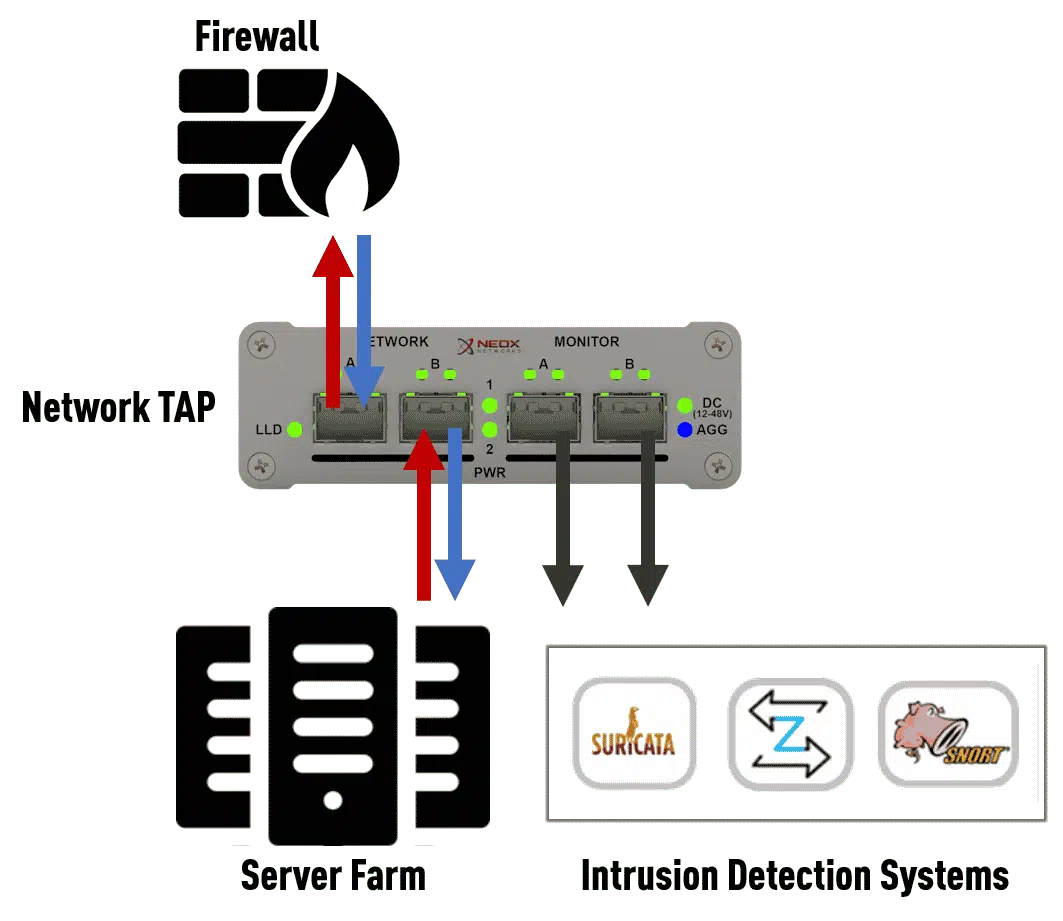
Intrusion Detection Systems (IDS)
An IDS analyses the network traffic and warns you of threats that might potentially cause damage to your network. To carry out this task effectively, you need a network connection that allows the IDS to examine all traffic.
You can’t protect your network traffic and sensitive data from threats without reliable network access points that provide you with the necessary data. It’s important that, by installing an IDS system, you don’t add any further errors to your network. The use of Network TAPs is recommended, therefore, as these devices provide a transparent copy of the data traffic running through your network and protect its integrity.
NEOX Networks’ Network TAPs provide all the right security features to make sure the IDS device provides data that’s free from errors without affecting your network.
Link failure propagation (LFP) is an important function that shuts down the Network TAPs connection on one side if it detects the connection has been lost on the other side. Furthermore, Network TAPs copy data from all OSI layers including corrupt data and network packets that aren’t IEEE 802.3-compliant, giving your security tools reliable information for precise and accurate security analysis.
More information on how to use Network TAPs can be found here.